NTP version 4 was first released in 2003, why haven’t you upgraded?
Network Time Protocol version 3 remains a security risk to the Internet and, unfortunately, there is a good chance that many people reading this post are part of the problem. Network Time Foundation released version 4 of the NTP daemon in August of 2003, a few years before the coinciding Request for Comments (RFC), 5905, was released in June of 2010. In other words, NTP version 4 has been around for more than a decade, and has been codified in RFC form for more than half a decade.
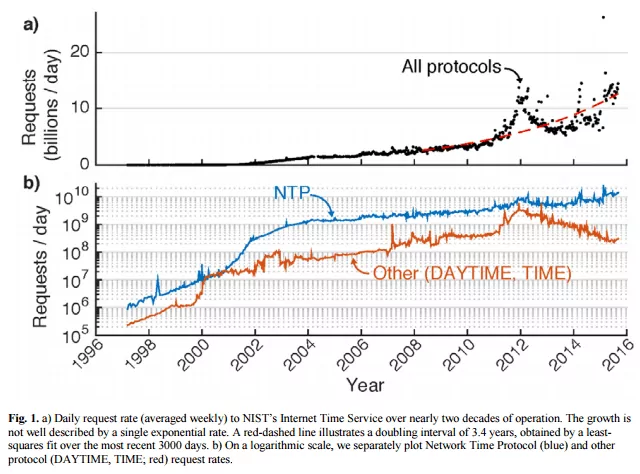
Despite the longevity of NTP version 4, a 2016 study conducted by the National Institutes of Science and Technology (NIST) about the NTP requests to their time servers found that 50.32% of the clients connecting to their Network Time Protocol service were still running NTP version 3. NIST operates 21 time servers, all of which are stratum-1 servers that are open to any device on the internet and time.nist.gov; (the round robin DNS name used for those servers) is, by far, the most used NTP destination on the internet. In early 2016, on a typical day, the NIST time servers fielded 16 billion NTP requests (that number is now over 20 billion) from 316 million unique IPv4 addresses. That traffic has continued to grow exponentially over the years as more devices that include support for NTP come online.
This is a problem for a number of reasons
Primarily because NTP version 3 is no longer maintained, so any security flaws uncovered are not patched and remain dangerously exploitable. The most commonly talked about exploitation of NTP version 3 is the use of monlist to launch DDoS attacks. This type of DDoS attack peaked in 2014 and has been on the decline since more ISPs started to implement BCP38. However, the infamous Mirai botnet has incorporated a number of NTP vulnerabilities into its cache of weaponized attacks and can exploit NTP daemons on vulnerable home routers, meaning that some NTP clients are still being used to launch DDoS attacks.
Of course, DDoS attacks are not the only security threat associated with NTP version 3. There are a number of remote code execution vulnerabilities that will allow an attacker to gain remote access, potentially remote root access, to a server or home router. In other words, an unpatched home router or public facing server running NTP version 3 could allow an attacker access to a victim’s network, and potentially give the attacker the ability to monitor all traffic leaving that network.
The big question is, why are there so many vulnerable devices still running today? Part of the problem has to do with the success of NTP. Network Time Protocol is a robust protocol that can run for years with no issues. If there are no problems with the NTP daemon, or its performance, it is not going to get the attention that other, more problematic, protocols get. Network Time Protocol is also an obscure protocol. Many people have no idea that they have a home router or home computer running a variant of the NTP reference daemon, so they don’t even know there is something that needs to be upgraded.

Nowhere is this problem more evident than in the home router market
There are generally two ways that consumers get a home router for their high-speed internet connection: The first is that they go to the store, pick one up, set it up and forget about it. Unless they lose connectivity and are forced to upgrade, there is a good chance that the software on that router will not be upgraded while it is in service. The second method is that the ISP sends a router to the consumer when they sign up for the service. In these cases, there is a pretty good chance that the ISP does not send the password or any instructions for accessing the router. The consumer assumes that the ISP is managing the router, but most of the time, the ISP is not. Which, again, means that the router sits for years without ever seeing an upgrade unless something goes wrong.
This is not to say that home routers are the only problem, but by all accounts, they appear to be the biggest problem when it comes to older versions of NTP. That being said, there are also millions of unpatched routers and servers in corporate networks that are either forgotten about or the maintenance has simply been ignored. These pose an even greater risk because they could allow access to corporate networks and contribute to the already rising number of breaches reported each year.
What can people do to improve the security of their systems running NTP?
First and foremost, upgrade to the latest version of NTP. At home, this means logging into the router and upgrading to the latest firmware or having the ISP enabling access to the router so the upgrade can be done. Call your ISP to see what you need to do. It also may mean doing a little bit of research. If the router vendor has not released new firmware in several years, it may be time to switch to a new router, one with a better security track record.
For corporations and organizations, securing Network Time Protocol often means first knowing all of the systems that exist in the network. Very often, systems running NTP in an organization go unpatched simply because the server, security or networking team did not know the system existed. Conducting regular network scans to find rogue systems and ensure they are properly patched is an important part of improving not just NTP security, but the security of the organization as a whole. Becoming an institutional member of Network Time Foundation will ensure that you are automatically notified of security releases.